Fraudulent communications
How to spot and avoid fraudulent communications (Phishing, Vishing and SmiShing).
About fraudulent communications
Cybercriminals will often use fraudulent communications to trick unsuspecting users into sending them their confidential data.
Examples of fraudulent communications seen by the University include:
- Phishing
- Vishing
- SMiShing.
Phishing
Phishing is a form of fraud that includes malicious emails.
They are designed to gain personal information and may appear to come from a genuine source, such as a streaming service, your bank, retailers like Amazon or someone you may know.
Emails often include links to bogus websites or attachments, which appear to be normal files (for example, Word, Excel or PDF) and are harmful.

How to spot Phishing
IT Services have technical controls in place to filter out spam before it reaches your inbox, but Phishing techniques change and some will inevitably get through.
- Check who sent you the email.
Be particularly suspicious of emails asking for personal or financial information. - Hover over any links to see where they will take you.
- Check the quality of emails.
Misspelling, poor punctuation and bad grammar are tell-tale signs of phishing. - Urgency.
Phishing emails will often have a sense of urgency as a social engineering technique. - Never respond to any email which asks for your account details or requests you to make a payment.
IT Services will never send you an email asking you to confirm your password.
Can you spot when you're being phished?
Phishing attacks attempt to trick unsuspecting users into revealing personal or financial information, often by mimicking content from well-known, trusted companies. Think you can tell what's real or fake?
Take the quizExamples of Phishing
Blue button Phishing email
![A screenshot of a blue button phishing email. From: a valid UWE or other contact address. To: your email address. Subject: Re: Invitation to take part in a research project - online survey. Warning message: If there are problems with how this message is displayed, click here to view it in a web browser. Body text: For: User Name, [blue button] 'Read Live Message' 13:54:59 Re: Invitation to take part in a research project - online survey Take action before Friday](/-/media/uwe/images/study/its/fraudulent-comms-examples-blue-button-1-614x365.png)
Signs that it is a phishing attack:
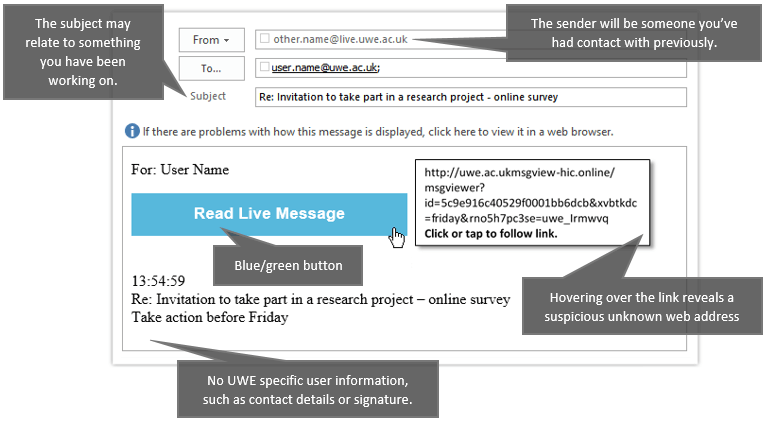
Fake warning from IT
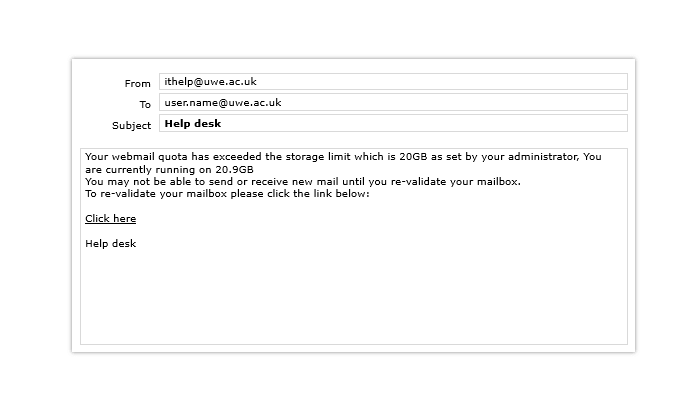
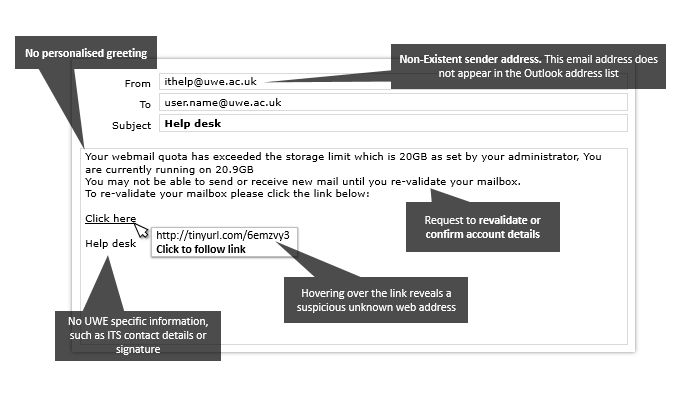
Signs that it is a phishing attack:
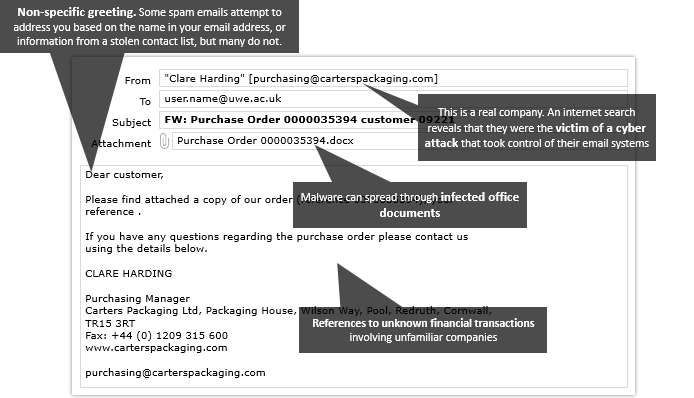
An email containing an infected document
![A screenshot of an email containing an infected document. From: Clare Harding [purchasing@carterspackaging.com]. To: user.name@uwe.ac.uk. Subject: FW: Purchase Order 0000035394 customer 09221. Attachment: Purchase Order 0000035394.docx. Body text: Dear customer, Please find attached a copy of our order (reference 0000035394), your reference. If you have any questions regarding the purchase order please contact us using the details below. Clare Harding, Purchasing Manager, Casters Packaging Ltd, Packaging House, Wilson Way, Pool, Redruth, Cornwall, TR15 3RT. Fax: +44 (0) 1209 315 600. www.carterspackaging.com, purchasing@carterspackaging.com](/-/media/uwe/images/study/its/fraudulent-comms-examples-infected-document-1-694x398.png)
Signs that it is a phishing attack:
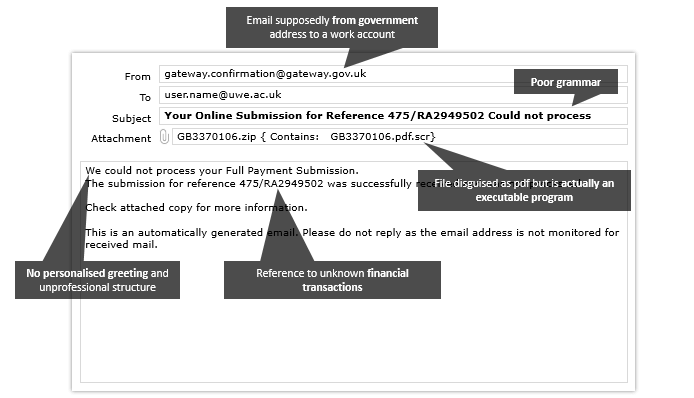
A document emailed from a government organisation
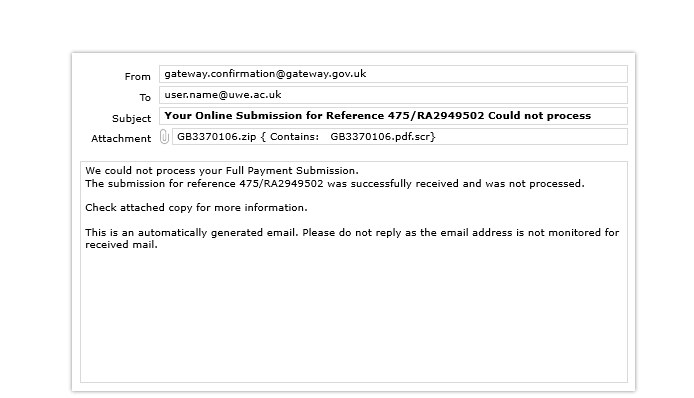
Signs that it is a phishing attack:
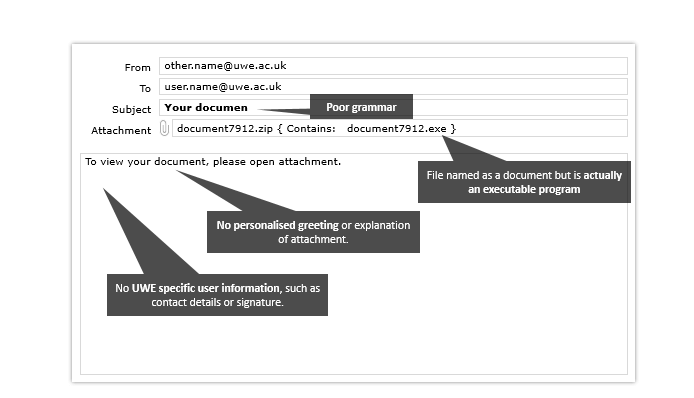
A document emailed form a UWE Bristol staff account
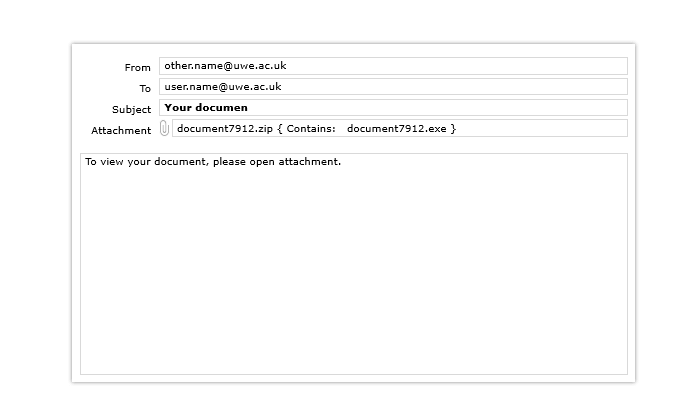
Signs that it is a phishing attack:
Vishing
Vishing or Voice Phishing is a type of fraudulent activity where criminals attempt to persuade victims to hand over personal details or transfer money over the phone.
Never give personal information (for example, passwords, banking details, credit cards details) over the phone to someone who has called you.
If you do receive such a call or you are in any doubt about the authenticity of the call, simply hang up. You can always phone the organisation back using a number from a verified source.

How to spot Vishing
Information: The criminals might not be very convincing and may know nothing about you. Alternatively, they could already have some information on you such as your name, address or phone number, but need a little bit more. This can create the impression that they seem very genuine.
Urgency: If you receive a call you will inevitably find that you will be hurried into providing them with the information that they need. They will do this to panic individuals in the hope you hand over your information without being able to think it through too much. Fear often leads people into acting without thinking.
Phone spoofing: This is when a phone number appears to be coming from a genuine source (for example, your bank or credit card company). This is a technique used by cybercriminals to hide their identity.
Remember, if you are in any doubt simply hang up and contact the organisation using a number from a verified source (such as a company website).
SMiShing
SMiShing or SMS Phishing is where text messages are sent trying to encourage people to pay money out or click on suspicious links. Sometimes attackers will try to get victims to call them by sending a text message with a specific number, with the intention to persuade them further.
SMSing scams are on the rise and are increasingly targeting students. Often these scam text messages are posing as the Student Loans Company and are asking students to verify bank details or their personal information—these messages look very authentic. This results in payments then being diverted to scammers bank account.
It is important to note that the SLC will never ask students to provide or verify their personal or financial information via email or text message. Find further information at Smishing scams are on the rise - GOV.UK.

How to spot SMiShing
Unsolicited text messages from unknown numbers should raise alarm bells. If you are in any doubt:
- delete the message
- contact the organisation using details from an alternative verified source (such as a company website).
You may also be interested in

Information Security Policies
All UWE Bristol users must read and abide by the information security policies and regulations.

Saving work in OneDrive
How and where to save you work (OneDrive).

Protect data and devices
Everyone must take steps to secure all their devices and data to reduce the risk of a data breach.
